Have questions or want to learn more about our solutions? Our team is here to help. We look forward to hearing from you!
Robin Verton and Pascal Verton are dedicated to developing innovative solutions that meet the demands of today’s digital landscape. With their expertise in IT-Security and UX-Design, they have made it their mission to simplify complex things.

IT-Security Expert with experience in the finance industry

UX-Design Expert
By using control cards, all relevant requirements – even those from different catalogs – are consolidated. Instead of having to answer the same question multiple times, a single response suffices and is automatically applied to all associated objects. This saves time, speeds up the compliance process, and ensures a consistent assessment across the entire security landscape.
Our dashboard gives you a real-time overview of the compliance status and outstanding tasks in your projects, clearly showing how many controls and analyses have already been fulfilled (“Compliant”) and where further action is needed (“Non-compliant”).
Recertification is vital for maintaining your organization’s security posture. Our system keeps track of upcoming due dates for controls and analyses, so you can review and update your measures as needed before they expire.
Our ready-to-use templates let you apply best practices instantly.
How it works:
You can expand or combine any template to suit your needs, saving time while leveraging proven best practices.
1. Identify Relevant Controls: If the BIA flags a process as critical, the system suggests matching controls (e.g., Business Continuity Plan).
2. Map Controls to Assets: Assign these controls to the tagged assets. The Critical tag ensures they inherit the right controls.
3. Monitor Gaps: Quickly see if any required controls are missing or incomplete, and act immediately to strengthen compliance.
1. Questionnaire Setup: Create a custom BIA questionnaire or import an existing one (e.g., via CSV).
2. Perform the Analysis: Attach the questionnaire to relevant processes or assets and gather responses to determine criticality and impact.
3. Review Results: The BIA outcomes are displayed on each asset, with any critical status or tag cascading through the asset hierarchy as needed.
1. Link Assets: Link your assets logically (e.g., Process – Application – Server – Database – Location) to create a clear structure and reflect dependencies. You can also import these relationships directly from existing systems (CSV or API), eliminating the need to rebuild them manually.
2. Assign Tags: Assign meaningful tags (e.g., DORA critical, GDPR) so that controls, reports, and other GRC processes can be applied more accurately and efficiently.
This way, subsequent processes – such as targeted analysis, reporting, or control management – can be carried out more accurately and efficiently.
We’d love to show you how Riskflow can streamline your security management. Contact us now via phone or email – we’re happy to help!
Different user roles (e.g., Administrator, Collaborator) can be assigned distinct permissions and responsibilities. This separation of duties supports better governance and reduces the risk of unauthorized changes or unwanted data access.
The software can be operated in the provider’s cloud, on local on-premises servers, or in a private (self-hosted) cloud environment. This flexibility allows you to choose the deployment model that best meets your security, compliance, and infrastructure requirements.
The audit log makes it possible to track at any time who made what changes and when, ensuring transparency and traceability.
Catalogs and analyses follow a structured lifecycle from draft to archive. In Draft mode, changes can be coordinated and quality improved, with the goal of publishing sufficiently quality-assured analyses and catalogs (Publish). Catalogs and analyses no longer needed are archived (Archive) but remain available for audits or references.
1. CSV Import: Upload a CSV file (e.g., assets.csv) to automatically populate fields such as ID, Name, and Location.
2. API Integration: Use our REST API (e.g., POST /api/assets) for real-time synchronization, ensuring your asset data is always up to date.)
3. Manual Entry: Quickly create individual assets through the user interface by entering details like Name, Category, and Description.
Work seamlessly with other teams – whether evaluating controls, storing evidence, or commenting on results. The primary focus here is the workflow, where the responder and the overseeing unit collaborate closely. All changes are synchronized in real time, ensuring everyone remains on the same page. No more endless Excel spreadsheets, just true collaboration in a centralized system.
Manage all evidence for your controls in one central location. Upload documents and document assessments to maintain an overview of your compliance status at all times. This way, everything is in one place, without having to search extensively.
Our Form Editor lets you define any type of analysis – whether it’s a Business Impact Analysis, a Risk Assessment, or a Compliance Checklist. Each form can output specific tags based on the responses entered. Once submitted, your assets automatically inherit the tags that correspond to their answers or calculated risk levels.
For instance, if a form identifies a process as “critical” that tag is immediately applied to the process and, if desired, cascades down to related systems or applications. This saves you from manual tagging and helps maintain a real-time, accurate view of your organization’s risk posture.
Want to get started quickly? Use one of our ready-made templates – like GDPR or ISO-specific questionnaires – or easily build your own. Our intuitive drag-and-drop editor ensures that anyone can create robust, automated analyses without writing a single line of code.
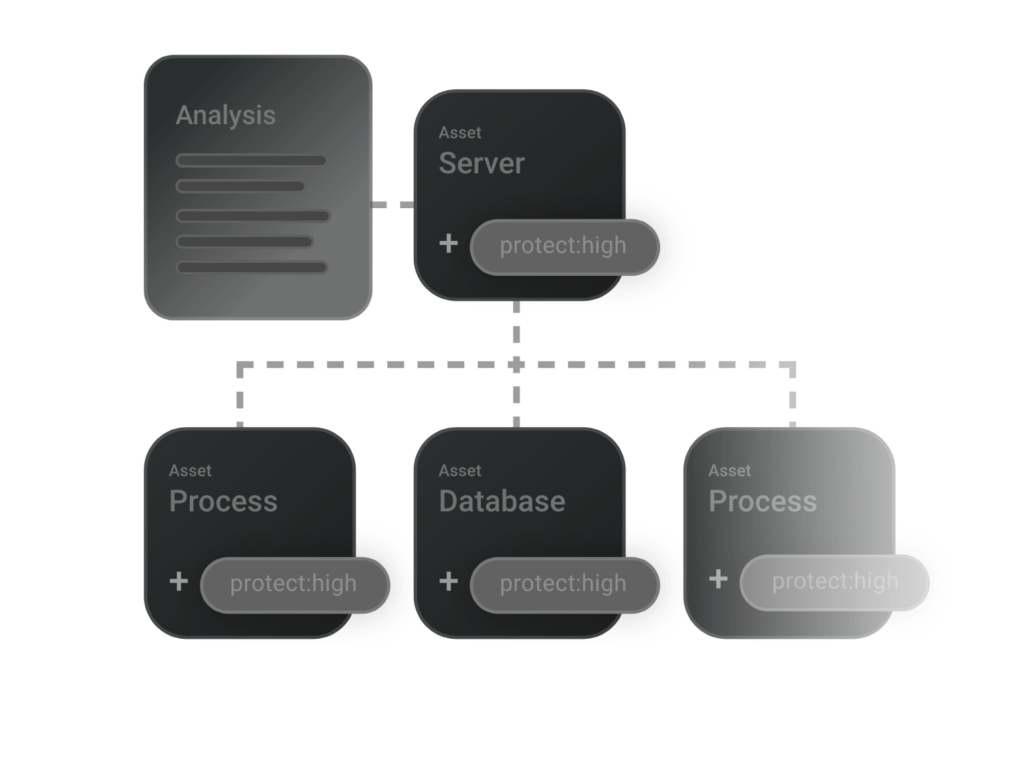
Imagine your Process is labeled dora:critical. All linked applications and databases automatically inherit this tag, ensuring you can quickly spot high-priority assets across your environment. In the screenshot, you can see how dora:critical, along with tags like dsgvo and stage:prod, flows down from the Process level to connected systems.
If there’s a particular asset you want to exclude – because it’s not truly critical in practice – you can simply disable inheritance for that asset. This way, you maintain an accurate overview of your real risk landscape without having to manually adjust every single item. Any disabled inheritance is properly logged, ensuring traceability and providing a clear audit trail for future reference.
Our platform is designed with an intuitive, user-focused interface that minimizes the learning curve and allows you to start working effectively right away. From streamlined navigation to context-sensitive help and guidance, every element is tailored to keep your team focused on high-value tasks rather than wrestling with complex menus or layouts.
Beneath this user-friendly surface lies a robust automation engine that takes care of repetitive or time-consuming processes. Whether it’s auto-synchronizing asset data, triggering updates based on newly identified risks, or automatically mapping controls to relevant tags, our platform helps you work smarter and faster – without compromising on accuracy or compliance.
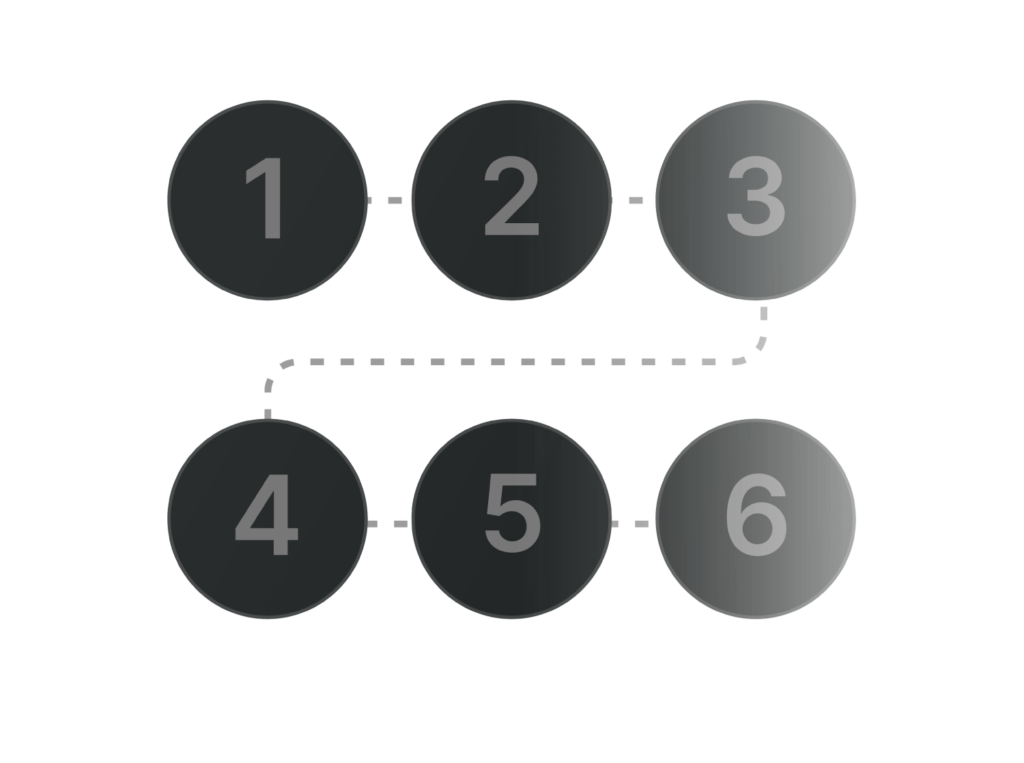
Our end-to-end approach begins with synchronizing or importing your assets so you have a solid, up-to-date foundation. Once captured, these assets are logically arranged and tagged, enabling clear insights into dependencies, ownership, and criticality. This streamlined setup lays the groundwork for deeper evaluations, such as Business Impact Analyses.
Building on these analyses, our solution automatically highlights relevant controls, tying them directly back to the assets in question. By mapping controls based on tags and criticality levels, you can efficiently identify gaps, allocate resources, and monitor progress. The result is a smooth, holistic process that delivers complete visibility and oversight – from asset registration to control implementation.
We operate from Germany, where businesses are accustomed to stringent regulatory requirements, ensuring that our software is built with a high level of compliance in mind. By locating our core operations in Europe, we not only adhere to Europe’s strict standards but also support and strengthen the local tech ecosystem.
In addition, our team has extensive experience dealing with various European compliance frameworks, making our solution well-suited for organizations facing complex or evolving regulations. This deep regulatory expertise underpins our commitment to delivering a product that addresses real-world compliance challenges.